Your employees are frequently exposed to sophisticated social engineering attacks. If these attacks get through your spam filters, a single employee can accidentally cost your business thousands of dollars . In addition, personal information about your clients and employees may be compromised, damaging your reputation and incurring legal and regulatory costs.
Human error is a leading cause of cybersecurity incidents and the Canadian Government recommends a cybersecurity training program as one of the fundamental security practices every organization should implement. Stratum has partnered with KnowBe4, the global leader in Security Awareness Training, to make building a cybersecurity training program for your company easy and effective. Are you prepared for cyberattacks targeting your critical work data? This questionnaire is for anyone who works away from their office, and for anyone who wants to improve the security of their digital devices. If any of your answers don't match our best practices (you'll find our recommended answers in bold), we can help. Cybercriminals do more than just steal data. Often, they destroy data, change programs or services, or use servers to transmit propaganda, spam, or malicious code. Increasingly, organizations are implementing multi-factor authentication (MFA) in their data security strategies. Working from home can be difficult. Follow these tips to keep your, and keep your company’s information secure. For more information read any of our other articles on security or give us a call. We are happy to help. With the growing concern around the COVID-19 virus, we are acutely aware that our position as an IT service provider makes us a potential vector for transmission:
We visit many offices across the Lower Mainland, interacting with hundreds of individuals on a monthly basis;
Keyboards, mice and phones all have a high potential for germ transmission.
In addition to following all Provincial and Federal recommendations, we have completed a WorkSafe COVID-19 Safety Plan. Additional pro-active measures we will be taking include:
Reducing the number of staff in our office by having some employees work from home;
Wearing masks when performing onsite visits;
Wiping down customer laptops and devices that our brought into our office for service with disinfectant wipes;
Putting a greater effort into resolving issues remotely and limiting onsite visits to issues which require it.
These measures will be effective until we receive further information or guidance from our Provincial and Federal health officials. While we don’t anticipate this will have a significant effect on your service experience, we do appreciate your patience and understanding. If you have any comments or concerns, please do not hesitate to contact us. A long time ago, Microsoft posted a TechNet article entitled "Ten Immutable Laws Of Security (Version 2.0)". The article has since been removed, but was valuable reading so we have preserved it verbatim here. Cyber risk is a reality of doing business in the 21st century and needs to be a significant part of every business’s risk management strategy. Understanding the cyber risk exposure and tolerance of your business is an important first step, but for many small and medium business directors these first steps into understanding cyber risk can be overwhelming. Fortunately, there are a few key activities that any business, regardless of size and budget, can undertake to reduce their cyber risk and improve their resilience to attacks. While not comprehensive, we believe they represent a significant and important first step toward building a cybersecurity program that effectively protects your business. The Canadian Centre for Cyber Security, part of the Communications Security Establishment, is Canada's authority on cybersecurity. Last week, they released a document outlining their baseline controls, which give guidance to small and medium Canadian businesses regarding to the most important technical and procedural steps to take (or "controls") to protect themselves. Microsoft is ending support for Windows 7 and Server 2008 based products on January 14, 2020. What does this mean for you? It seems data breaches are continually in the news. How can you protect yourself? Often, when attackers breach one website, they are able to move laterally to other, more secure sites because users re-use their password.
Common advice is to use a strong, unique password for every service you use. Is this possible, what constitutes a strong password? Ransomware has been a growing problem. This is a form of malware which encrypts your files and extorts money for the decryption key.
With the recent worldwide outbreak of the "WannaCry" strain of ransomware on the news, we've compiled a couple general tips on keeping your systems safe. We have come to expect Public Wi-Fi to be available almost everywhere, often connecting blindly to any unsecured network claiming "Free Public Wi-Fi".
But is it safe to do so? SciShow has produced a short video explaining some of the risks and things you should be aware of. A key component of security in the digital age is awareness. Often, it is not the technology that presents the biggest vulnerabilities to scammers and criminals, it is users. This is the principle that the classes of attacks known as "phishing" and "social engineering" are based on.
A keystone of "social engineering" attacks is the exploitation of trust. The attacker will pose as someone in a position of authority, or posessing some knowledge that grants them credibility. They will then use this false credibility to gain access and information from others who are deceived by their trick.
The "CEO Email Scam" is an example of this. Windows 10 is gradually being released to the public. Some users, who have pre-registered already have it. We've compiled some things to know when considering the upgrade. When you think of the IT department, what comes to mind? Is it a group of people you'd like to spend time with?
Establishing a relationship with our customers is key to our success at Stratum. In order to be your IT department, we need to integrate with your team, and calling IT can't be a chore. Our staff is the personality of our company. When it comes to the essential technologies that your business processes depend on, there can be no compromises. Failed hardware means downtime, and downtime means lost productivity.
We are committed to providing the highest quality hardware available. Our recipe for reliability has three key ingredients. In a competitive marketplace, technology cannot be an afterthought. Your technology infrastructure must grow with your business, and we want to be there for the long haul. We will help you plan for growth, and we will be there to make sure your technology keeps pace with your business.
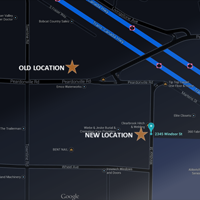
Stratum Systems is moving to a new location. Don't worry, it's not far away. We will be operating from the new office as of May 5, 2014 .
Our new location is more visible from the road and easier to access.
#5 2345 Windsor Street Abbotsford, BC V2T 6M1 Microsoft is ending support for Windows XP in April of this year, and for Windows Server 2003 in July of 2015. What does this mean for you? We are often asked about how best to optimize a website for high search engine rankings online. This is commonly called "SEO". We'll often warn those who ask that while there are certain measures you can take, many "SEO Companies" employ techniques that do more harm than good. Look for an SEO company that focuses on generating useful content rather than applying the SEO snake oil of the day.
Along those lines, Smashing Magazine posted an excellent article with tips about optimizing your business website's content. Every business should have off-site backups. We are happy to be able to fulfill that need, offering automatic online backups to our customers.
Automatic Online Backups eliminate the hassle of manually taking tapes or external drives home. Stratum’s online backups automatically back your data up nightly. Data is encrypted prior to transmission, and remains encrypted even while stored in an ISO certified Canadian datacenter. We’re excited to announce that Stratum Systems and Prism PC have merged! Both companies have been serving customers in the Lower Mainland since 2007.
The new company will be operating as Stratum Systems. What role could information technology and online health services (Health IT) play in our healthcare system? A recent study done by The Conference Board of Canada and Canada Health Infoway (CHI) indicates the Health IT's role could be larger than we think. It estimated that Canadians could boost economic output by $408 million and save more than 70 million man hours per year by incorporating and properly integrating Health IT into Canada’s healthcare system. Stratum Systems supports the City of Abbotsford ‘City of Character’ Initiative. We believe sticking to our values we, as a community, will improve our city and we will develop into a City of Character. Many businesses want to use technology to boost their effectiveness, efficiency and profitability and give them a competitive edge in the market. However, they don’t know what technology they should get, or how they will use it. When upgrading your business with new technology there are a few things to consider: what are your current competitive advantages, and what you need to be able to do your job better, faster and more effectively. Many of our customers are using Cobian Backup as a low-cost, easy to manage backup solution. Cobiansoft has recently released a beta version of Cobain Backup 11. A key enhancement that we're excited about is the option to force full backups to occur on a particular week day (a feature that was conspicuously missing in previous versions). Google is changing their privacy policies. Read the article for full details. A key note is that your Web History , if it's turned on, will be merged with other services like YouTube.
If you'd rather not have your Web History shared with other Google services, you can turn it off before the new policy comes into effect on March 1st, 2012. Finally, a refreshed look for the Stratum Website! The old design was getting a little dated. We hope the new site will be an effective vehicle for communication about news, alerts and updates that are important to our customers.
Let us know what you think of the new layout. Are you considering moving to Electronic Medical Records? We have successfully transitioned dozens of doctors to EMR, and worked with many systems including Intrahealth Profile , Osler Systems , EMIS (now aquired by QHR), Optimed Accuro EMR , Wolf Medical Systems , Klinix and more. The most common infections we see these days are those caused by fake or "rogue" anti-virus applications. Also known as "scareware", these programs will try to scare you into giving up credit card information by displaying fake virus alerts and claiming that you must purchase some software to clean up your computer. There has been a recent trend of telephone scams targeting computer users. This scam is known to target both home and business users.
To help you protect yourself from this threat we have compiled some information on how the scammers operate. As of this writing, we at Stratum Systems are entering into our 5th year of business. I'd like to take this opportunity to reflect on our beginnings. 
Security Awareness Training

Working from Home Security Questionnaire

Secure Your Data with Multi-Factor Authentication

Security Tips when Working from Home

COVID-19 Prevention Measures

Ten Immutable Laws Of Security

Cybersecurity First Steps

New Cybersecurity Guidance for Canadian Businesses

Windows 7 and Server 2008 End-of-Life

What's in a password?

Ransomware

Is Public Wi-Fi Safe?

CEO Email Scams

Windows 10: What you Should Know

The Personality of an IT Department

No Compromises: Our commitment to Quality

A Place to Grow
We are Moving!

Windows XP and Server 2003 End-of-Life

Tips for Writing Business Content for the Web

Stratum Systems Online Backups

Stratum Systems and Prism PC have Merged!

Efficient health I.T. could save $408 million

Stratum Systems is a proud supporter of Abbotsford’s "City of Character" Initiative

Leveraging Technology to Increase Your Competitive Advantage

Cobian Backup 11 (Gravity) Beta Release
Google Privacy Policy Change

New Look Online

Considering E.M.R.?

Beware of "Rogue" Anti-Virus

Phone Scam Warning

Our History
Previous page: Cybersecurity Next page: Jobs
